- CISO Series Newsletter
- Posts
- Join us tomorrow for "Hacking SOC Workflow"
Join us tomorrow for "Hacking SOC Workflow"
Join us TOMORROW, Friday [01-09-26], for "Hacking SOC Workflow"
Join us Friday, January 9, 2026, for “Hacking SOC Workflow: An hour of critical thinking of evolving security operations.”
It all begins at 1 PM ET/10 AM PT on Friday, January 9, 2026 with guests Jason Shockey, CISO, Cenlar FSB, and Edward Wu, CEO and founder, Dropzone AI. We'll have fun conversation and games, plus at the end of the hour (2 PM ET/11 AM PT) we'll do our meetup.
Thanks to our Super Cyber Friday sponsor, Dropzone AI
Defense in Depth
What Makes a Successful CISO?
The role of the CISO is still relatively new in the C-Suite. Given its newness, the role's definition appears to vary by industry and business. What should the expectations be for the CISO role?
Check out this post by Richard Seiersen of Qualys for the discussion that is the basis of our conversation on this week’s episode, co-hosted by David Spark, the producer of CISO Series, and Edward Contreras, senior evp and CISO, Frost Bank. Joining them is Ejona Preci, group CISO, LINDAL Group.
Listen to the full episode here.
Consequence, not controls
Technical controls and compliance metrics have long defined cybersecurity, but that framing misses the real game being played. "Being a CISO isn't about systems. It's about consequence authority. Who owns it, who hides from it, and who gets blamed when the music stops," said Eric Staffin of Staffin Cyber Risk Associates. "Most CISOs aren't empowered to touch consequence architecture—they're stuck patching the perimeter while the business runs wild with exposure they'll never see until it detonates." The challenge isn't just structural, it's conceptual. Alexander Rogan of Abatis pointed out a mismatch between a CISO's authority and accountability, saying that "many boards and C-suites still fundamentally misunderstand what cyber risk is. They don't see it as enterprise risk; they see it as an IT problem with compliance obligations."
The credibility gap
Leadership without technical grounding creates a dangerous vacuum in which bad advice sounds as credible as good. "A CISO should be a cybersecurity expert who transitioned to a cybersecurity risk and strategy executive," said Segun Adeshina of Symbotic. "There is a natural path between deep expertise and strategic vision. CISOs can't lead strategic conversations without credibility that comes from lived experience." Thomas Zeppa of the U.S. Department of Housing and Urban Development echoed this concern from direct observation: "A CISO is a business leader but also needs at least some technical background. I've seen career manager CISOs listening to the wrong people because they didn't have a solid background in the field to know if someone was selling them BS or providing actual value."
Defining the undefined
The CISO role suffers from a fundamental lack of definition, creating confusion for both practitioners and the organizations that hire them. "The CISO role IS COMPLETELY undefined in general," said Jordan M. Schroeder of Arxa Cyber. "And while that presents ambiguity between CISOs in different contexts, it presents an opportunity for organisations to properly define what is needed, and what is needed from them, for their CISO to succeed in their context." Emma Höij of ChangeAbility observed that this ambiguity in hiring practices leads to disappointment, saying, "In my experience, many organizations hire CISOs blindly, thinking the CISO will teach them everything and fix everything. Instead of supporting the discussion, based on real knowledge about what security is and what security and IT aren't. The hiring managers and boards somehow know exactly what they want. But don't know what they need. And they call it a 'CISO'."
Expanding the mandate
The CISO's scope is evolving beyond traditional security boundaries into territories that require new partnerships and competencies. "The modern CISO is not only responsible for digital resilience—but increasingly for the integrity of machine-assisted decision-making," said Eckhart M. of GIZ GmBH. "They must ensure that AI systems are explainable, resilient against adversarial inputs, and aligned with regulatory and ethical expectations. This requires collaborating with data science, legal, and compliance teams to govern algorithmic risk." This expansion reflects a broader truth about executive roles. Steve Albee of Albert noted that "if you have a C in your title, then you should be doing whatever the company needs you to do. Just as there is no single definition of what a CEO should do for their company, the role of the CISO will vary based on the organizational context, maturity, industry, and strategic priorities."
Please listen to the full episode on your favorite podcast app, or over on our blog, where you can read the full transcript. If you’re not already subscribed to the Defense in Depth podcast, please go ahead and subscribe now.
Huge thanks to our sponsor, ThreatLocker.
Subscribe
Subscribe to Defense in Depth podcast
Please subscribe via Apple Podcasts, Spotify, YouTube Music, Amazon Music, Pocket Casts, RSS, or just type "Defense in Depth" into your favorite podcast app.
LIVE!
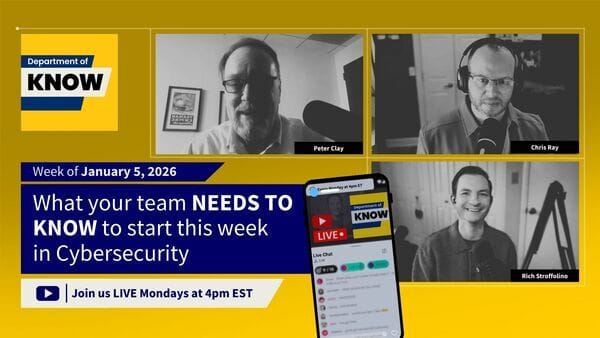
Cybersecurity Headlines - Department of Know
Our LIVE stream of The Department of Know happens every Monday at 4 PM ET / 1 PM PT with CISO Series producer Richard Stroffolino, and a panel of security pros. Each week, we bring you the cybersecurity stories that actually matter, and the conversations you’ll be having at work all week long.
Monday’s episode featured Chris Ray, field CTO, GigaOm, and Peter Clay, CISO, Aireon. Missed it? Watch the replay on YouTube and catch up on what’s shaping the week in security.
Join us again next week, and every Monday.
Thanks to our Cybersecurity Headlines sponsor, Hoxhunt
Cyber chatter from around the web...
Jump in on these conversations
“The blackout in Venezuela was likely caused by a cyber offense” (More here)
“Europe has ‘lost the internet’, warns Belgium’s cyber security chief” (More here)
“How do you stay current in cybersecurity” (More here)
Coming up in the weeks ahead on Super Cyber Friday:
[01-09-26] “Hacking SOC Workflow”
[01-23-26] “Hacking Past Mistakes”
Save your spot and register for them all now!
Thank you for supporting CISO Series and all our programming
We love all kinds of support: listening, watching, contributions, What's Worse?! scenarios, telling your friends, sharing in social media, and most of all we love our sponsors!
Everything is available at cisoseries.com.
Interested in sponsorship, contact me, David Spark.